Unraveling Blockchain Security: The Snooping Attack
This post is part of my Blockchain Security series which I initially started off in my LinkedIn page, but now I have decided to move the series into the stacked-stories page.
The Snooping Attack: An Overview
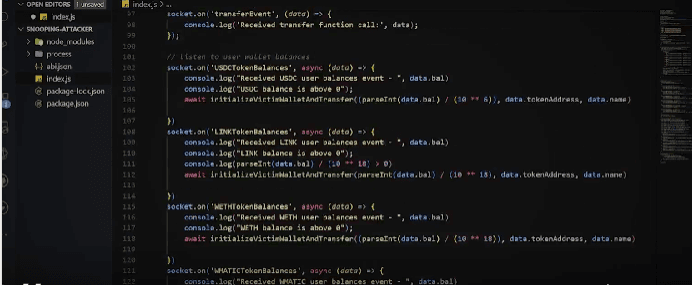
The Snooping Attack is a devious exploit that revolves around an attacker gaining access to your private key. Instead of directly unlocking your wallet funds through conventional means like Metamask, the attacker takes a more cunning approach. They leverage technologies like Node.js or other applications to tirelessly monitor your wallet activity. Specifically, their focus is on keeping a watchful eye on your token and cryptocurrency balances.
How It Works ?
When there's an increase in any of your asset balances, the program kicks into action using the pilfered private key. This triggers a transfer function, swiftly siphoning off all the funds from the victim's account into the attacker's deposit account.
A Practical Demonstration
To offer a tangible understanding of the Snooping Attack, I've put together a small project that simulates this exploit. Watch the accompanying video to witness this attack in action - Watch Here
Stay tuned for the upcoming parts of this series, where we'll delve into even more captivating topics related to blockchain security. If safeguarding your assets and understanding potential threats and vulnerabilities in the blockchain realm piques your interest, make sure to keep up with my posts and join in on the discussions.
For those eager to explore the inner workings of this attack further, you can find the corresponding GitHub repository here.
With this introduction to the Snooping Attack, we've embarked on a journey to fortify our understanding of blockchain security. Together, we'll navigate through various exploits, fortifications, and strategies to keep our assets safe in this dynamic landscape.
Stay vigilant, and I look forward to our continued exploration of blockchain security in the next installment of this series!